CoreOS Bolsters Container Platform With Crypto ‘Trust’

A stumbling block to broader adoption of micro-services in general and application containers in particular has been ensuring the overall security of infrastructure while running business-critical applications housed in containers. Hence, there has been an early emphasis on isolating container-based applications as a way to bolster security while scaling the number of containers that can be hosted, for example, on a single virtual machine.
While industry momentum around Docker containers continues to build, upstart CoreOS is attempting to take container security a step further by adding a "cryptographic chain of trust" extending from the application layer to the hardware that delivers enterprise applications. The San Francisco-based container security specialist unveiled the enterprise version of its Tectonic container platform with "distributed trusted computing" during an industry event in New York on Wednesday (Dec. 2).
Tectonic is underpinned by Google's (NASDAQ: GOOG) Kubernetes, the open source container orchestration system used to manage clusters of Linux containers (Google is an investor in CoreOS.) Tectonic combines the commercial distribution of the CoreOs software stack with Kubernetes, released to all by the search engine giant in mid-2014. Tectonic is intended to stabilize infrastructure to get application containers into production and running on enterprise platforms.
CoreOS said this week its trusted computing approach adds a layer of hardware-driven cryptographic verification that validates the distributed application layer, containers and the operating system. At a higher level, the enterprise version of Tectonic is intended to secure infrastructure across layers and machines as well as from hardware to application containers and ultimately to the distributed application cluster.
The trusted computing approach "harnesses both hardware and software to isolate and cryptographically verify and audit containers executing on clusters of Secure Booted nodes," the company explained in recent white paper.
Another selling point highlighted by CoreOS is that its trusted computing approach ensures that hardware is only running software it is authorized to run. As a way to preserve openness and avoid vendor "lock-in," CoreOS stressed that its approach allows customers to put their cryptographic keys into the firmware on their servers. "This means the servers can run only the software explicitly authorized by the enterprise, and nothing else," the company said.
"Rather than taking away freedom or flexibility, our implementation builds on top of customer-controlled keys embedded in their server firmware," explained Matthew Garrett, a security software engineer at CoreOS. That approach allows operators "to specify and verify exactly what software their systems run."
Along with the Kubernetes cluster manager, which allows only secure-booted machines into the cluster, the CoreOS trusted platform includes its "rkt" (short for Rocket) container runtime that verifies a secure configuration as well as the CoreOS commercial version of Linux. Hardware components include the firmware in which customer keys are embedded along with a "trusted platform module" that delivers a secure audit log for everything that has been booted.
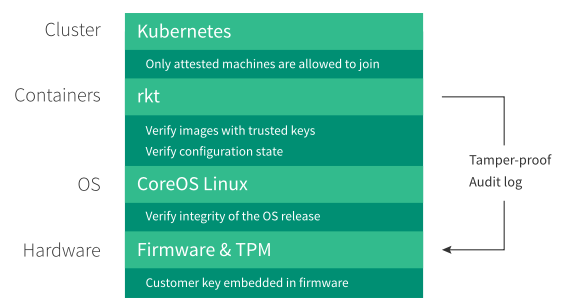
Tectonic with "distributed trusted computing". (Source: CoreOS)
The result, CoreOS CEO Alex Polvi asserted in a statement, is "cryptographically guaranteed end-to-end integrity and control of [the container] environment."
The trusted computing upgrade to Tectonic is being made available as a configuration for Tectonic users and is optimized for bare metal configurations, the company said. CoreOS also announced a partner, Cloudflare, a provider of content delivery networks and distributed domain names servers.
Related
George Leopold has written about science and technology for more than 30 years, focusing on electronics and aerospace technology. He previously served as executive editor of Electronic Engineering Times. Leopold is the author of "Calculated Risk: The Supersonic Life and Times of Gus Grissom" (Purdue University Press, 2016).











