When Vendors Don’t Play Nice, the Enterprise Loses
Microsoft is leading the way to the future of the enterprise business model. This might be hard to believe considering the company’s track record of locking users into its ...Full Article
Cray Forecasts More Enterprise Contracts
Global supercomputer maker Cray's recent deals with Danish and Swiss meteorological organizations further cemented its leadership in the weather business, but Cray predicts blue skies ahead for expanding sales ...Full Article
Tools Reveal Enterprises’ Dirty Little Cybersecurity Secrets
By leveraging publicly available information, companies like BitSight and SecurityScorecard rate most businesses' cybersecurity profiles, information third parties like CISOs, CSOs, CIOs, insurers, investors, financiers, employees and, perhaps, cyber ...Full Article
Updated: HP Enterprise Will Cut 25,000 to 30,000 Jobs
Even before it gets off the ground, HP Enterprise – one of the two companies HP will split into by year’s end – is getting its wings clipped: HP ...Full Article
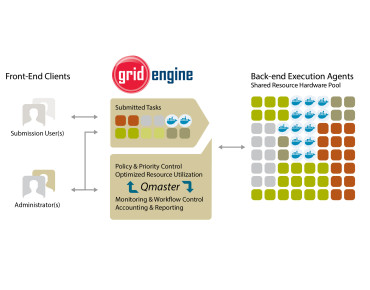
Univa Grid Engine Takes On Docker Orchestration, Scheduling
Workload management and optimization solutions developer Univa is entering the Docker orchestration frenzy with today's release of the Univa Grid Engine Container Edition product. In September 2014, Univa told EnterpriseTech ...Full Article
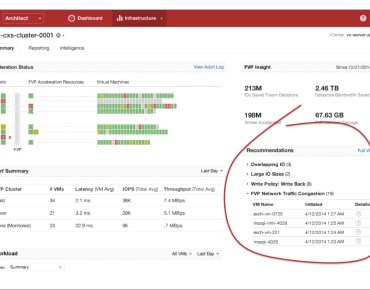
PernixData Decouples Performance, Management from Storage
PernixData aims to further simplify storage managers' jobs with today's release of FVP version 3.0, Freedom, and software platform Architect. The company's technology decouples storage performance and management functions ...Full Article
Salesforce Debuts IoT Cloud: For the Internet of Customers
With its newly announced Salesforce IoT Cloud, Salesforce looks to expand far beyond its traditional customer relationship management (CRM) and sales roots to become the central hub for the ...Full Article
Achieving High Performance Computing without the Supercomputer
When most hear the term "High-Performance Computing" or HPC, what often comes to mind is the image of well-funded research laboratories, think CERN’s Large Hadron Collider, where the sheer ...Full Article
HP Enterprise’s Bill Mannel Talks HPC, Intel, Big Data, and More
As vice president and general manager of high performance computing and big data for Hewlett Packard Enterprise for almost a year, Bill Mannel oversees two fast-growing and complementary areas ...Full Article
Caringo FileFly Cuts Storage TCO, Simplifies Data Access
A consistent, growing challenge enterprises face in the big data age revolves around decreasing the total cost of ownership for storage while simultaneously providing ready access to petabytes of ...Full Article